Extremist actors
Academic Publications
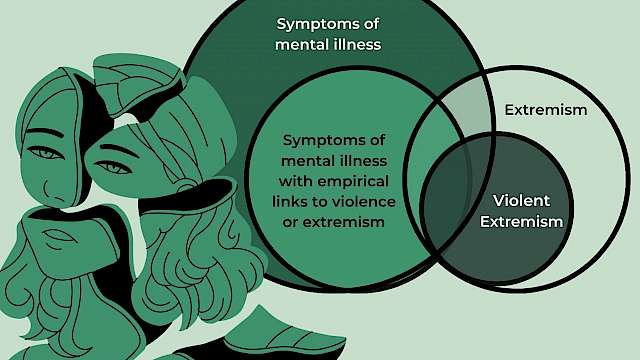
The development of structured guidelines for assessing risk in extremist offenders
This paper describes a methodology developed by the National Offender Management Service (NOMS) to assess risk and needs in convicted extremist offenders in England and Wales, and for the assessment of those offenders for whom there are credible concerns about their potential to commit such offences. A methodology was needed to provide an empirically-based systematic and transparent approach to the assessment of risk to inform proportionate risk management; increase understanding and confidence amongst front-line staff and decision-makers, and facilitate effective and targeted intervention. It outlines how the methodology was developed, the nature of the assessment, its theoretical underpinnings, the challenges faced and how these have been addressed. Learning from casework with offenders, from government commissioned research and the wider literature is presented in the form of 22 general factors (with an opportunity to capture additional idiosyncratic factors, i.e., 22+) that contribute to an individual formulation of risk and needs that bears on three dimensions of engagement, intent and capability. The relationship of this methodology, the Extremism Risk Guidelines (ERG 22+) with comparable guidelines, the Violent Extremism Risk Assessment 2 (VERA version 2) and the Multi-Level Guidelines (MLG), is also discussed. This paper also considers the ERG’s utility, validity and limitations.
(From the journal abstract)
Lloyd, M., & Dean, C. (2015). The development of structured guidelines for assessing risk in extremist offenders. Journal of Threat Assessment and Management, 2(1), 40–52.
Staying Engaged in Terrorism: Narrative Accounts of Sustaining Participation in Violent Extremism
Research exploring radicalization pathways and how and why people become involved in terrorism has expanded since the 9/11 attacks. Likewise, over the last decade research exploring de-radicalization and desistence from terrorism has grown and expanded in an attempt to promote exit from extremist or terror groups.
However, research studies on how individuals sustain engagement in terrorism and their involvement with extremist organizations, often in the face of great adversity, are absent from the body of research.
To address this scarcity of research this study analyzed accounts of engagement in violent extremism produced by Northern Irish loyalist and republican paramilitaries in order to explore how their paramilitary lifestyle, perpetration of acts of political violence and the pressure from countering threats posed by rival groups, and the State security forces impacted on them.
The analysis utilized a hybrid of thematic analysis and interpretative phenomenological analysis (IPA). The themes raised through the analysis reflected the psychological, social and economic hardship associated with this lifestyle. The narrative accounts also illustrated psychological changes associated to engagement in violence and from insulation within tightly knit extremist groups.
As most of the participants faced incarceration during their paramilitary careers, themes also reflected on the impact imprisonment had on them. The themes explored factors that sustained their involvement, including the role of identity development and identity fusion in sustaining their extremism, the impact of insulated group membership, feelings of efficacy, dehumanization processes, community support, and beliefs in the utility of violence.
(From the journal abstract)
Neil Ferguson & James W. McAuley, 2020. Staying engaged in terrorism: narrative accounts of sustaining participation in violent extremism. Frontiers in psychology.
https://doi.org/10.3389/fpsyg.2020.01338
Community reporting on violent extremism by 'intimates': emergent findings from international evidence
To promote early intervention strategies, Countering/Preventing Violent Extremism (C/PVE) policies internationally seek to encourage community reporting by 'intimates' about someone close to them engaging in terrorist planning.
Yet historically, we have scant evidence around what either helps or hinders intimates to share concerns with authorities. We address that deficit here through a state-of-the-art assessment of what we currently know about effective related C/PVE approaches to community reporting, based on key findings from a groundbreaking Australian study and its UK replication.
The consistency of qualitative findings from nearly 100 respondents offers new paradigms for policy and practice.
(From the journal abstract)
Paul Thomas, Michele Grossman, Kris Christmann, and Shamim Miah, 2020. Community reporting on violent extremism by 'intimates': emergent findings from international evidence. Critical Studies on Terrorism. https://doi.org/10.1080/17539153.2020.1791389
ISIS Propaganda: A Full-Spectrum Extremist Message
This book offers a comprehensive overview and analysis of the Islamic State's use of propaganda.
Combining a range of different theoretical perspectives from across the social sciences, and using rigorous methods, the authors trace the origins of the Islamic State's message, laying bare the strategic logic guiding its evolution, examining each of its multi-media components, and showing how these elements work together to radicalize audiences' worldviews.
This volume highlights the challenges that this sort of "full-spectrum propaganda" raises for counter terrorism forces. It is not only a one-stop resource for any analyst of IS and Salafi-jihadism, but also a rich contribution to the study of text and visual propaganda, radicalization and political violence, and international security.
(From the book abstract)
Stephane J. Baele, Katharine A. Boyd, and Travis G. Coan. 2020. ‘ISIS Propaganda: A Full-Spectrum Extremist Message’. Oxford, New York: Oxford University Press. ISBN: 9780190932459
Terrorist Decision Making in the Context of Risk, Attack Planning, and Attack Commission
Terrorists from a wide array of ideological influences and organizational structures consider security and risk on a continuous and rational basis. The rationality of terrorism has been long noted of course but studies tended to focus on organizational reasoning behind the strategic turn toward violence. A more recent shift within the literature has examined rational behaviors that underpin the actual tactical commission of a terrorist offense. This article is interested in answering the following questions: What does the cost–benefit decision look like on a single operation? What does the planning process look like? How do terrorists choose between discrete targets? What emotions are felt during the planning and operational phases? What environmental cues are utilized in the decision-making process? Fortunately, much insight is available from the wider criminological literature where studies often provide offender-oriented accounts of the crime commission process. We hypothesize similar factors take place in terrorist decision making and search for evidence within a body of terrorist autobiographies.
(From the journal abstract)
Paul Gill, Zoe Marchment, Emily Corner, and Noémie Bouhana. 2018. ‘Terrorist Decision Making in the Context of Risk, Attack Planning, and Attack Commission’. Studies in Conflict & Terrorism: https://doi.org/10.1080/1057610X.2018.1445501.
Violent Extremism: A Comparison of Approaches to Assessing and Managing Risk
The task of assessing and managing risk of violence has evolved considerably in the last 25 years, and the field of violent extremism has the potential to stand on the shoulders of the giants of this time. Therefore, the objective of this study was to identify good practice in the risk field and to apply that to the specific area of risk in relation to violent extremism – in order that developments here accord to highest standards of practice achieved so far elsewhere.
Method and Results
We begin by addressing the essential requirement to define the task of assessing and managing the risk of violent extremism – What is its purpose and parameters, who are its practitioners, in what contexts is this activity delivered, and how might any such context both facilitate and hinder the objectives of the task? Next, we map the terrain – What guidance is already available to assist practitioners in their work of understanding and managing the risk of violent extremism, and by what standards may we judge the quality of this and future guidance in the contexts in which is it applied? Finally, we explore options for the development of the field in terms of the empirical basis upon which the risks presented by individuals and the organizations to which they may affiliate are assessed, understood, and managed.
Conclusions
Recommendations are proposed in relation to each of these three areas of concern with a view to supporting the rapid and credible advancement of this growing and vital area of endeavour.
(From the journal abstract)
Caroline Logan and Monica Lloyd. 2019. ‘Violent Extremism: A Comparison of Approaches to Assessing and Managing Risk’. Legal and Criminological Psychology, 24 (1): 141–61. https://doi.org/10.1111/lcrp.12140.
Telling Stories of Terrorism: A Framework for Applying Narrative Approaches to the Study of Militant’s Self-Accounts
Narrative has recently garnered much attention in the study of terrorism but remains poorly understood. This paper offers some initial steps towards translating the promise of narrative approaches into a set of steps for systematically analysing and understanding terrorists’ own accounts of their engagement with extremism and militancy. This approach rests on the assumption that terrorist authored accounts are more than post-hoc rhetorical exercises that aim to persuade others, or even the authors themselves, of the righteousness of their political cause or otherwise mitigate their responsibility for their involvement in violence. In particular, I advance a framework for methodically applying narrative approaches to terrorist authored texts, in particular, autobiographies. In doing so, I will demonstrate how this approach can help better comprehend how individuals involved in militancy understand the world, draw upon existing narrative resources and give meaning to their actions.
(From the journal abstract)
Simon Copeland. 2018. ‘Telling Stories of Terrorism: A Framework for Applying Narrative Approaches to the Study of Militant’s Self-Accounts’. Behavioral Sciences of Terrorism and Political Aggression: 1–22. https://doi.org/10.1080/19434472.2018.1525417.
The Internal Brakes on Violent Escalation: A Typology
Most groups do less violence than they are capable of. Yet while there is now an extensive literature on the escalation of or radicalisation towards violence, particularly by ‘extremist’ groups or actors, and while processes of de-escalation or de-radicalisation have also received significant attention, processes of non- or limited escalation have largely gone below the analytical radar.
This article contributes to current efforts to address this limitation in our understanding of the dynamics of political aggression by developing a descriptive typology of the ‘internal brakes’ on violent escalation: the mechanisms through which members of the groups themselves contribute to establish and maintain limits upon their own violence. We identify five underlying logics on which the internal brakes operate: strategic, moral, ego maintenance, outgroup definition, and organisational.
The typology is developed and tested using three very different case studies: the transnational and UK jihadi scene from 2005 to 2016; the British extreme right during the 1990s, and the animal liberation movement in the UK from the mid-1970s until the early 2000s.
(From the journal abstract)
Joel Busher, Donald Holbrook & Graham Macklin 2018. ‘The internal brakes on violent escalation: a typology’. Behavioral Sciences of Terrorism and Political Aggression 10.1080/19434472.2018.1551918
The Rise and Fall of the English Defence League: Self-Governance, Marginal Members and the Far Right
What determines the success or failure of far-right organisations? This article uses new qualitative data to explain the sudden rise and subsequent decline of the English Defence League, an anti-Islamic, street protest organisation established in the UK in 2009.
We explain the rise and fall of the English Defence League through the lens of the theory of collective action to show that the English Defence League initially motivated activism by supplying selective incentives that were enhanced by the participation of others.
The pursuit of ‘participatory crowding’ led to indiscriminate recruitment into the organisation that enabled numbers to expand into the thousands, but ultimately caused the English Defence League’s downfall because it resulted in the presence of large numbers of ‘marginal members’ with low levels of commitment whose subsequent exit was decisively destructive.
Self-governance mechanisms to ensure greater loyalty from members could have prevented the English Defence League’s decline but would also have limited its initial success.
(From the journal abstract)
Morrow, Elizabeth A, and John Meadowcroft. 2018. ‘The Rise and Fall of the English Defence League: Self-Governance, Marginal Members and the Far Right’. Political Studies, June. https://doi. org/10.1177/0032321718777907.
Psychological and Behavioral Examinations of Online Terrorism
It has long been recognised that terrorists make use of the internet as one of many means through which to further their cause. This use of the internet has fuelled a large number of studies seeking to understand terrorists' use of online environments.
This chapter provides an overview of current understandings of online terrorist behavior, coupled with an outline of the qualitative and quantitative approaches that can and have been adopted to research this phenomenon. The chapter closes with a discussion of the contentious issue of ethics in online terrorism research.
The aim of the chapter is to equip readers with the necessary knowledge and skills to conduct their own research into terrorists' online behavior, taking best ethical practices into consideration when doing so.
(From the book abstract)
Prentice, Sheryl, and Paul J. Taylor. 2018. ‘Psychological and Behavioral Examinations of Online Terrorism’. In Psychological and Behavioral Examinations in Cyber Security, edited by John McAlaney, 151–71. https://www.igi-global.com/chapter/psychological-and-behavioral-examinations-of-online-terrorism/199887.
Same Kind of Different: Affordances, Terrorism, and the Internet
The rapid development of the Internet as a cornerstone of private and social life has provoked a growing effort by law enforcement and security agencies to understand what role the Internet plays in terrorism. Paul Gill, Emily Corner, Maura Conway, Amy Thornton, Mia Bloom, and John Horgan's (2017, this issue) effort to identify empirically when and how terrorists engage with the Internet is thus timely and important.
Understanding when terrorists use the Internet is valuable for investigators who must evaluate the immediacy of the risk posed by a suspect or cell. Knowing the typical patterns of use (or lack of use) can facilitate inferences about a cell's preparedness, the nature of its support, and even the goal of its attack. Understanding how terrorists use the Internet is essential for policy makers who must construct legislation to deter citizens from terrorism while retaining their rights to freedom.
This is arguably best accomplished by legislation targeted at a narrow set of Internet uses that are, as far as possible, exclusively associated with illegal actions.
In this policy essay, we focus on two of Gill et al.’s (2017) main contributions. We argue that, subject to robust independent replication, they encourage thought about the functions of the Internet for terrorists, which in turn may have implications that offer useful guidance for policy and practice. Alongside the article's conceptual contributions, Gill et al. also assert to have resolved several pragmatic challenges and we suggest ways in which their solutions, if developed fully, could offer value to the security analyst community. Finally, we take stock of where Gill et al.’s contribution has left us and review the next steps.
(From the journal abstract)
Taylor, Paul J., Donald Holbrook, and Adam Joinson. 2017. ‘Same Kind of Different’. Criminology & Public Policy 16 (1): 127–33. https://doi.org/10.1111/1745-9133.12285.