Comment

Article
Pip Thornton
Words as Data: The Vulnerability of Language in an Age of Digital Capitalism
Article
| 5 min read

Article
Ryan Boyd, Paul Kapoor
Psychological Profiling and Event Forecasting Using Computational Language Analysis
Article
| 5 min read

Article
Debi Ashenden
Data and the Social and Behavioural Sciences
Article
| 4 min read

Article
Lorraine Hope, Wayne Thomas
A to Z of Influence Tactics and Topics
Article
| 4 min read

Article
Gordon Wright, Nelli Ferenczi
Cross-cultural dimensions impacting persuasion and influence in security contexts
Article
| 4 min read

Article
Robert Nash
In the misinformation age, remember that your memories might be fake news
Article
| 5 min read
Article
Stephan Lewandowsky, Sander van der Linden, John Cook
Can we inoculate against fake news?
Article
| 4 min read

Article
Emily Corner
Mental Disorder in Terrorism, Mass Murder, and Violence: Moving away from Pathologising Grievance
Article
| 5 min read

Article
Emily Alison, Laurence Alison
Persuasion and Influence or Genuine Connection and Rapport
Article
| 5 min read

Article
Samantha McGarry
The Far Right and Reciprocal Radicalisation
Article
| 4 min read

Article
Susan Brandon
Using Stereotypes to Prepare for Interviews
Article
| 4 min read
Article
Robert Cialdini, Steve Martin
The Power of Persuasion and Pre-Suasion to Produce Change
Article
| 5 min read

Article
Wayne Thomas, Lorraine Hope
Try To See Things My Way? The Role Of Perspective Taking In Eliciting Information
Article
| 4 min read

Article
Rosalind Searle, Charis Rice
Positively Influencing Individuals During Organisational Change
Article
| 15 min read

Article
Kirk Luther, Brent Snook, Timothy Moore
Lingering Problems With The Mr Big Technique
Article
| 5 min read

Article
Heather Flowe
Informants Under The Influence: Can Intoxicated Informants Provide Accurate Information?
Article
| 3 min read

Article
Simon Henderson
The Trade Of The Tricks: How Principles Of Magic Can Contribute To National Security
Article
| 5 min read

Article
Christopher McDowell
Displacement and Transition Risks
Article
| 4 min read

Article
Sheryl (Prentice) Menadue
Influence In Extremist Messaging
Article
| 4 min read
Article
Andrea Pereira, Jay Van Bavel
The Partisan Brain: Why People Are Attracted To Fake News And What To Do About It
Article
| 5 min read

Article
David Neequaye
Subtle Influence and Information disclosure: How Priming Works in Intelligence Interviews
Article
| 4 min read

Article
Paul Taylor
Communicating across cultures
Article
| 10 min read
Article
Nicola Power
Terror attacks: How psychological research can help improve the emergency response
Article
| 4 min read

Article
Suzanne Newcombe
Disengagement: Lessons from Cults and Sectarian Groups
Article
| 4 min read
Article
Simon Wells
Transitions in negotiation: From crisis to success
Article
| 6 min read
Article
Sarah Marsden
Reintegrating Extremists: ‘Deradicalisation’ and Desistance
Article
| 5 min read

Article
Jordan Nunan, Becky Milne
Turning research into practice in investigative interviewing
Article
| 3 min read

Article
Aldert Vrij, Ronald P. Fisher
Which Lie Detection Tools are Ready for Use?
Article
| 4 min read

Article
Rosalind Searle, Charis Rice
How Messing with Employee Pensions Can Backfire on Companies
Article
| 4 min read

Article
Martin Innes
Russian Influence And Interference On Twitter Following The 2017 UK Terrorist Attacks
Article
| 3 min read

Poster
Lorraine Hope
Mind map: What sources mean when they say "I Don't Know"
Poster
| 2 min read

Article
David Omand
Intelligence ethics: not an oxymoron
Article
| 5 min read

Article
Tina Wilchen Christensen
From extremists to democratic citizens
Article
| 6 min read

Article
Nicola Power
A to Z of Decision Making
Article
| 4 min read

Article
Samantha Mann
How does a smuggler behave?
Article
| 4 min read

Article
Miriam Oostinga
Communication error handling in suspect interviews and crisis negotiations
Article
| 3 min read

Article
Jan-Willem Bullée
Social Engineering: From Thoughts to Awareness
Article
| 3 min read

Article
Neil Ferguson
Understanding Engagement in Violent Extremism in Northern Ireland
Article
| 3 min read

Article
Laurence Alison, Michael Humann, Sara Waring
Communicating with casualties in emergencies
Article
| 3 min read

Article
Paul Gill
8 things you need to know about terrorist decision-making
Article
| 4 min read
Article
Julie Gore, Paul Ward, Gareth Conway
Naturalistic Decision Making and Uncertainty
Article
| 2 min read

Article
Simon Ruda
Measuring decision making
Article
| 4 min read

Article
Renate Geurts
Why professionals are needed to assess threats of violence
Article
| 3 min read

Article
Nicola Power
Decision making during emergencies: what have we learned and where do we go from here?
Article
| 4 min read
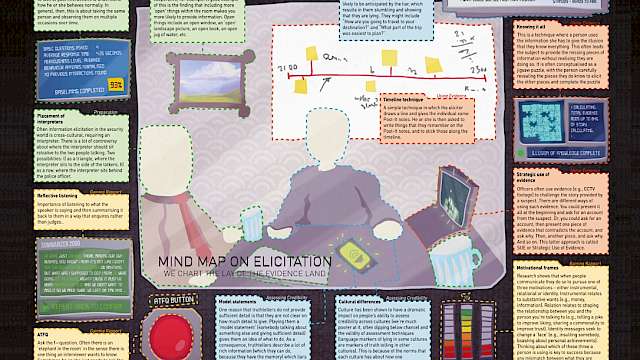
Poster
Paul Taylor
Mind map: Information Elicitation
Poster
| 3 min read
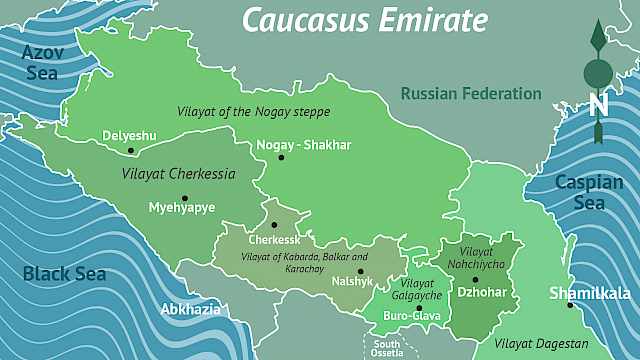
Article
Cerwyn Moore, Mark Youngman
New report on Russian-speaking Foreign Fighters
Article
| 2 min read

Article
Jasjit Singh
Sikh Activism in Britain
Article
| 4 min read

Article
Jasjit Singh
Religious transmission among young adults in the digital age
Article
| 4 min read

Article
Awais Rashid, Sylvain Frey
Cyber security decisions: how do you make yours?
Article
| 3 min read