Comment

Article
Mark Youngman
Learning from ideological variance and change
Article
| 3 min read

Article
Michele Grossman, Paul Thomas
What are the barriers to reporting people suspected of violent extremism?
Article
| 3 min read
Article
Martin Everett
Covert Networks
Article
| 2 min read

Article
Rosalind Searle, Charis Rice
Trust and Insider Threat: Ensuring We Don’t Look Back – or Forward – in Anger
Article
| 3 min read
Article
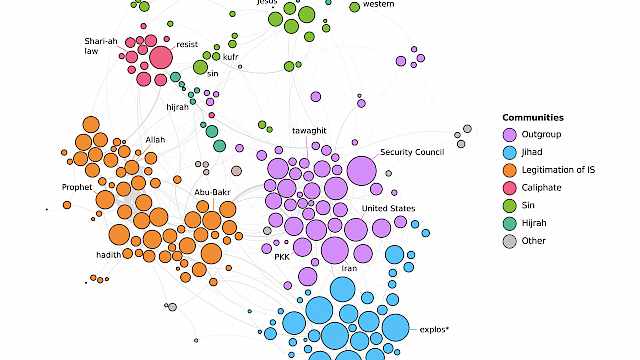
Stephane Baele, Katharine Boyd, Travis Coan
Extremist Prose as Networks
Article
| 3 min read

Article
Kate Muir
What is rapport and how can you increase it?
Article
| 3 min read

Article
Mia Bloom
Islamic State messaging on Telegram
Article
| 3 min read

Article
Michele Grossman, Paul Thomas
Community Reporting: The key to defeating terrorism?
Article
| 4 min read

Article
Thilo Gross
Things that spread: Epidemics on networks
Article
| 4 min read
Article
Using Networks to Predict the Impact of ‘Bad Apples’ on Team Performance
Article
| 3 min read

Article
Dorothy Carter, Cynthia Maupin
Leadership Is a Social Network: Implications for Security
Article
| 4 min read

Article
Katharina Karcher
Can female participation in political violence lead to social progress? – a case study from Germany
Article
| 3 min read
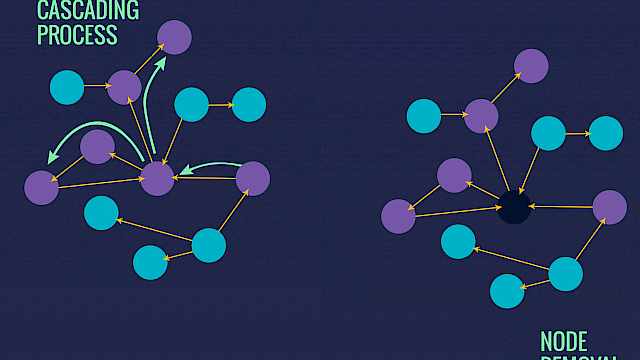
Article
Christos Ellinas
Predicting and Preparing for the Failure of Complex Systems
Article
| 4 min read
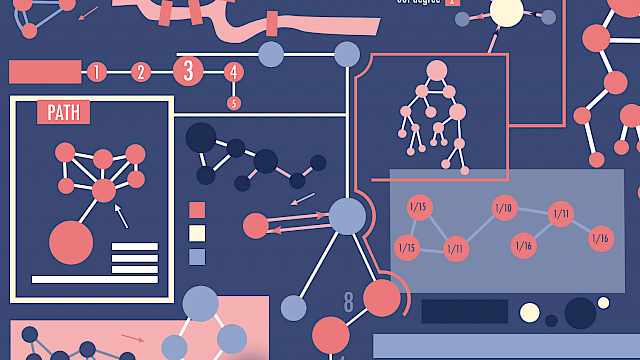
Poster
Adam Joinson
Mind Map: The Bluffers Guide To Networks
Poster
| 3 min read

Article
Adam Joinson, Brittany Davidson
Why networks matter
Article
| 3 min read

Article
Jordan Nunan
Gathering Full and Faithful Human Intelligence
Article
| 3 min read

Article
Ben Lee
Understanding the far-right landscape
Article
| 2 min read

Article
Charis Rice, Rosalind Searle
Trust and Citizenship: The Insider Threat
Article
| 3 min read

Article
John Horgan
The Lost Boys
Article
| 6 min read

Article
Mark Youngman
Lessons from the decline of the North Caucasus insurgency
Article
| 4 min read

Article
Donald Holbrook
The Islamic State and Ayman al-Zawahiri’s ‘alternative jihad’
Article
| 3 min read

Article
Nicholas Ryder
Is there something missing? Terror finances and the UK review of economic crime
Article
| 3 min read

Article
Nelly Lahoud
What Next for Islamic State?
Article
| 4 min read

Article
Christopher McDowell
Sri Lanka, Diaspora Politics, and The End of Violence
Article
| 4 min read

Article
Cerwyn Moore
Transnational Activism Through the Ages
Article
| 3 min read
Article
Feni Kontogianni
Memory recall: The challenge of eliciting reliable information
Article
| 3 min read

Article
Olivia Brown
Teamwork in extreme environments
Article
| 3 min read
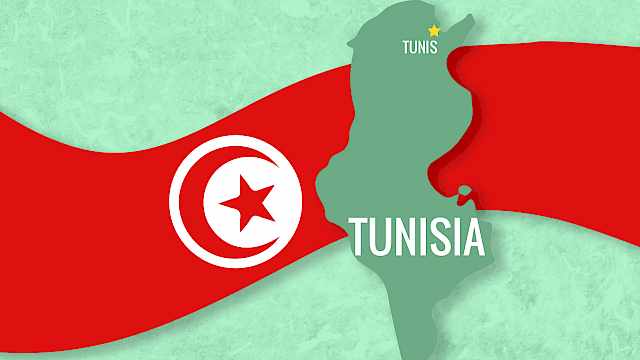
Article
George Joffé
Regional Guide: Tunisia
Article
| 3 min read
Article
Wolfram Lacher
Regional Guide: Libya
Article
| 3 min read

Article
Kris Christmann
Manchester attack: an 'arms race' against ever adapting terror networks
Article
| 4 min read

Article
Michael Axworthy
Regional Guide: Iran
Article
| 3 min read

Article
Joas Wagemakers
Regional Guide: Jordan
Article
| 3 min read

Article
Elisabeth Kendall
Regional Guide: Yemen
Article
| 4 min read

Article
Paul Taylor
7 Things Worth Knowing About Groups
Article
| 4 min read

Article
Joe Uscinski
Everyone is a conspiracy theorist
Article
| 4 min read

Article
Cerwyn Moore, Timothy Holman
Remainers and leavers: Foreign fighters after the ‘Islamic State’
Article
| 5 min read

Article
Iain Edgar
After Islamic State: the place of night dream inspiration and propaganda
Article
| 2 min read

Article
Emma Williams
What Makes People Susceptible to Malevolent Influence Online?
Article
| 3 min read

Article
Rosie Mutton
The role of gender in violent extremism
Article
| 3 min read

Article
Mark Youngman
After St Petersburg: Russia and the Threat from Central Asian Terror Networks
Article
| 5 min read

Article
Lynn Weiher
How do we measure rapport in interviews?
Article
| 3 min read

Article
James Lewis
How do teachers engage with Prevent?
Article
| 4 min read

Article
Simon Copeland
The Importance of Terrorists’ Families and Friends
Article
| 4 min read
Article
Mark Youngman
Russia's domestic terrorism threat is serious, sophisticated, and complex
Article
| 4 min read

Article
Ben Lee
Grassroots counter messaging in the UK
Article
| 3 min read

Article
Irina Tache
Connecting Culture to Deception Detection
Article
| 4 min read

Article
Kim Knott, Matthew Francis
Are converts to Islam more likely to become extremists?
Article
| 5 min read

Article
Kim Knott, Ben Lee
How does the family pass on religion?
Article
| 3 min read

Article
Simon Copeland
Transmitting Terrorism: A Family Affair?
Article
| 3 min read