Comment

Article
Emma Williams, Debi Ashenden
Phishing Scams Are Becoming Ever More Sophisticated And Firms Are Struggling To Keep Up
Article
|4 min read
Article
Amanda van Eck Duymaer van Twist
How beliefs may come and go: a brief overview of a ‘cult career’
Article
|3 min read

Article
Sarah Marsden
From ideological material to targeting choice in leaderless jihadist
Article
|3 min read

Article
Aristotle Kallis
‘Reverse waves’: how radical ideas spread and take hold
Article
|4 min read

Article
Ben Lee
A different perspective on CVE
Article
|4 min read

Article
Ben Lee, Elizabeth Morrow
Transmission in context
Article
|4 min read
Article
Jonathan Scourfield
Learning to be a Muslim
Article
|3 min read

Article
John F. Morrison
Transmitting Legitimacy and Victimhood: Violent Dissident Irish Republicanism
Article
|3 min read

Article
Lynn Davies
Disrupting transmission of extremist messages through education
Article
|3 min read

Article
Kim Knott
Why transmission?
Article
|3 min read

Article
Lorraine Hope, Matthew Francis
When does inconsistency matter?
Article
|2 min read

Article
Matthew Williams, Pete Burnap
Cyber crime and the social web
Article
|3 min read

Article
Debi Ashenden
Employees Behaving Badly
Article
|4 min read

Article
Lorraine Hope
How does memory work?
Article
|3 min read

Article
Joanne Hinds
What is the role of technology in an emergency?
Article
|4 min read

Article
Linda Woodhead
The continuing growth of religious extremism and how to counter it
Article
|6 min read

Article
René Rydhof Hansen, Lizzie Coles-Kemp
Everyday Security: A Manifesto for New Approaches to Security Modelling
Article
|3 min read

Article
Tim Stevens
Cyber security and the politics of time
Article
|4 min read

Article
Marcus Rogers
Hacker Mindset
Article
|3 min read
Article
Jeremy Watson, Emil Lupu
PETRAS: Cyber Security of the Internet of Things
Article
|3 min read

Article
Christian Meissner, Susan Brandon
Expanding the frontiers of interrogation research and practice
Article
|3 min read

Article
Debi Ashenden
Fact Check: The Cyber Security Attack Surface
Article
|4 min read
Article
Heather Shaw, David Ellis
Apple or Android? What your choice of operating system says about you
Article
|2 min read

Article
Nicholas Ryder
The Criminal Finances Bill
Article
|4 min read

Article
Ben Lee
Understanding the counter-jihad
Article
|2 min read
Article
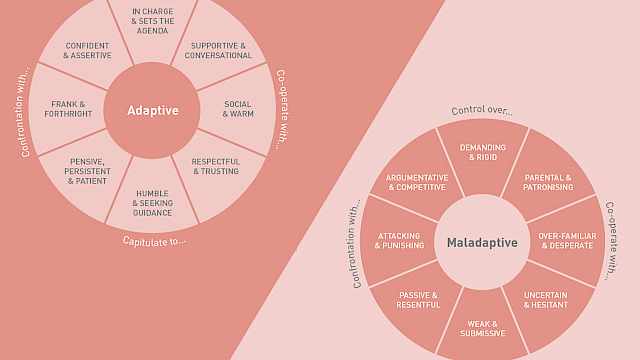
Laurence Alison, Michael Humann, Sara Waring
Building good rapport in interviews
Article
|4 min read

Article
Debi Ashenden
Creativity and Cyber Security
Article
|2 min read

Article
Paul Taylor
The A–Z of Information elicitation
Article
|3 min read

Article
Robert A. Fein
Improving practice through research: The US and the Study on Educing Information
Article
|2 min read
Article
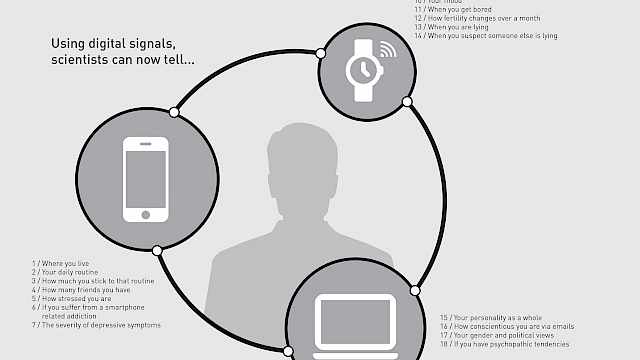
David Ellis, Lukasz Piwek
The future of wearable technology
Article
|2 min read

Article
Elizabeth Morrow
Loyal footsoldiers: The attractions of EDL activism
Article
|5 min read

Article
Adam Joinson, Emma Williams
Eliciting Information Online
Article
|3 min read

Article
Paul Taylor
The promise of social science
Article
|3 min read

Article
Simon Oleszkiewicz
Eliciting information the friendly way: Conceptualising the Scharff Technique
Article
|3 min read

Article
Becky Milne
Let them be heard: Enabling communication and recall of forensic interviewees
Article
|1 min read

Article
Lorraine Hope
Memory at the sharp end: the psychology of eliciting information
Article
|1 min read

Article
Emma Barrett
The role of trust in deciding which terrorist faction to join
Article
|2 min read

Article
Sheryl (Prentice) Menadue
How Technology Could Help Predict Terrorist Attacks
Article
|3 min read

Article
Nicholas Ryder
Where does the Islamic State get its money?
Article
|4 min read
Article
Cerwyn Moore, Elizabeth Morrow
What role do women play in violent extremism?
Article
|3 min read

Article
Kim Knott
What are the Five Pillars of Islam?
Article
|3 min read

Article
Emma Barrett, Matthew Francis
The Cognitive Interview: How Research has improved Practice
Article
|2 min read

Article
Nicola Power
Joint Decision Making in Real-World Emergencies: Recommendations for Improving the Joint Decision Model
Article
|4 min read

Kim Knott, Matthew Francis
What’s the difference between Sunni and Shi’a Muslims?
3 min read

Article
Joanne Hinds
How Does Phishing Work?
Article
|3 min read

Article
Emma Barrett, Matthew Francis
Terrorists’ use of messaging applications
Article
|3 min read

Article
Ben Lee
One peaceful march doesn't change Pegida's disturbing ideology
Article
|3 min read

Article
Debi Ashenden
Your Employees: The Front Line in Cyber Security
Article
|10 min read

Article
Matthew Francis
Research drives understanding and disruption of terrorism
Article
|4 min read
