
Cyber Security
This issue highlights research on everyday insider threats to organisations, the threat from cyber-enabled and cyber-dependent crimes, and the hacker mindset.
- CREST Security Review
- Issue 1 : Eliciting Information
- Issue 2 : Cyber Security
- Issue 3 : Transmission
- Issue 4 : After Islamic State
- Issue 5 : Networks
- Issue 6 : Decision-Making
- Issue 7 : Transitions
- Issue 8 : Influence
- Issue 9 : Data
- Issue 10 : Stress And Resilience
- Issue 11 : Risk
- Issue 12 : COVID-19
- Issue 14 : Trust
- Issue 13 : Technology
- Issue 15 : Trauma
- Issue 16 : Innovation
- Issue 17 : Misinformation
- Issue 18 : Communication

Article
Emma Barrett, Matthew Francis
Terrorists’ use of messaging applications
Article
| 3 min read
Article
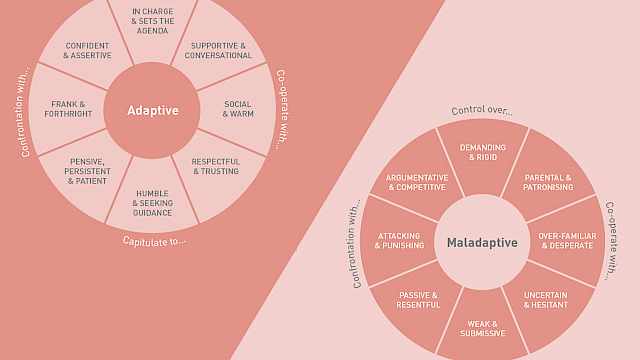
Laurence Alison, Michael Humann, Sara Waring
Building good rapport in interviews
Article
| 4 min read
Article
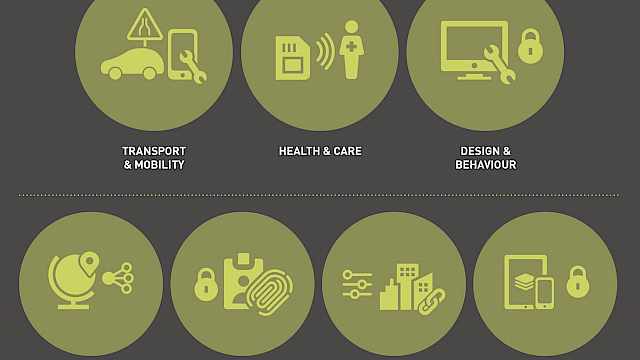
Jeremy Watson, Emil Lupu
PETRAS: Cyber Security of the Internet of Things
Article
| 3 min read

Article
Debi Ashenden
Employees Behaving Badly
Article
| 4 min read

Article
René Rydhof Hansen, Lizzie Coles-Kemp
Everyday Security: A Manifesto for New Approaches to Security Modelling
Article
| 3 min read

Article
Tim Stevens
Cyber security and the politics of time
Article
| 4 min read

Article
Matthew Williams, Pete Burnap
Cyber crime and the social web
Article
| 3 min read

Article
Marcus Rogers
Hacker Mindset
Article
| 3 min read

Article
Joanne Hinds
What is the role of technology in an emergency?
Article
| 4 min read

Article
Christian Meissner, Susan Brandon
Expanding the frontiers of interrogation research and practice
Article
| 3 min read

Article
Elizabeth Morrow
Loyal footsoldiers: The attractions of EDL activism
Article
| 5 min read

Article
Linda Woodhead
The continuing growth of religious extremism and how to counter it
Article
| 6 min read

Article
Debi Ashenden
Fact Check: The Cyber Security Attack Surface
Article
| 4 min read