Resources
new
Report
Lotta Rahlf
Historical Context and the Good Lives Model
Report
| 
Report
James Lewis, Sarah Marsden, James Hewitt, Anne Peterscheck
Trauma, Adversity & Violent Extremism: A Systematic Review
Report
| 
Report
James Hewitt, Anne Peterscheck, Sarah Marsden, James Lewis
Trauma, Adversity & Violent Extremism: Workshop Report
Report
| 
Special
Nicola Power, Mark Levine, Richard Philpot, Jennifer Alcock
Bridging the Principle-Implementation Gap: Evaluating organisational change to achieve interoperability between the UK Emergency services
Special
| 
Guide
Nicola Power, Mark Levine, Richard Philpot, Jennifer Alcock
The Psychology Of Interoperability - Study Two Summary
Guide
| 
Report
Nadine Salman, Zainab Al-Attar, Grace McKenzie
Practitioner Perspectives on Counterterrorism and Neurodiversity
Report
| 
Report
Nadine Salman, Zainab Al-Attar
Autism and Extremism: The Questions that Operational Practitioners Should be Asking
Report
| 
Report
Nadine Salman, Zainab Al-Attar
Neurodivergence and Violent Extremism: 18 International Case Studies
Report
| 
Report
Nadine Salman, Zainab Al-Attar
A Systematic Review of Neurodivergence, Vulnerability, and Risk in the Context of Violent Extremism
Report
| 
Report
Nicola Power, Jennifer Alcock, Richard Philpot, Mark Levine
The Psychology of Interoperability: A Systematic Review of Joint Working Between the UK Emergency Services
Report
| 1 min read
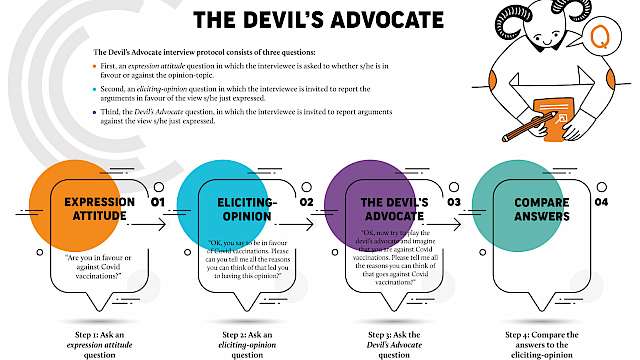
Poster
Aldert Vrij, Sharon Leal
The Devil's Advocate interview protocol
Poster
| 
Guide
Aldert Vrij, Sharon Leal
Verbal indicators of omission lies
Guide
| 
Guide
Aldert Vrij, Sharon Leal
The Devil’s Advocate Approach
Guide
| 
Report
Simon Copeland
Narratives, techniques, and pathways: How the Islamic State Khorasan Province recruits Afghan students online
Report
| 
Poster
Rachel Monaghan, Bianca Slocombe, John Cuddihy, Neale Gregg
Prosecuting extremists in the United Kingdom Q&A
Poster
| 
Report
Hanna Paalgard Munden, Sarah Marsden, Md Kamruzzaman Bhuiyan, Lotta Rahlf, Hanna Rigault Arkhis, Aimee Taylor
Good Lives in Right-Wing Extremist Autobiographies
Report
| 
Article
Ben Lee
Risky Business? Siege, subcultures, risk, and unintended consequences
Article
| 
Article
Mujammil Hussain, Jordan Nunan
Understanding Islam and Rapport Building with Muslims
Article
| 
Report
Ben Lee
LARPocalypse: Part One - Siege as a Subculture
Report
| 
Special
Nicola Power, Mark Levine, Richard Philpot
The Psychology of Interoperability: A Systematic Review and Case Study from the UK Emergency Services
Special
| 
Report
Rachel Monaghan, Bianca Slocombe, John Cuddihy, Neale Gregg
Prosecuting Extremists in the UK: An Exploration of Charging, Prosecution, and Sentencing Outcomes
Report
| 
Report
Anastasia Kordoni, Shengnan Liu, Miriam Koschate-Reis, Mark Levine
Detecting Hybrid Social Identities: A Computational Analysis of Influence & Resilience in Online (RWE) Communities
Report
| 
Report
Zoe Marchment, Paul Gill
How robust is the evidence base for the human ability to recognise suspicious activity/hostile reconnaissance?
Report
| 
Report
Ben Lee, Sarah Marsden
LARPocalypse: Part Three - Subcultural Constraint
Report
| 
Report
Ben Lee
LARPocalypse: Part Two - Differential Participation in Siege Culture
Report
| 
Report
James Lewis, James Hewitt, Sarah Marsden
Lived Experiences of Contact with Counter-Terrorism Policies and Practices
Report
| 
Report
Rosie Mutton, James Lewis, Sarah Marsden
Public Mitigation of Terrorism Risk: A Rapid Review of the Literature
Report
| 
Report
Rosie Mutton, James Lewis, Sarah Marsden
Online Radicalisation: A Rapid Review of the Literature
Report
| 
Report
James Lewis, Sarah Marsden
Secondary Countering Violent Extremism (CVE) Interventions: A Rapid Review of the Literature
Report
| 
Report
Emily Winterbotham, Jessica White, Claudia Wallner, David McIlhatton
Evaluation Approaches for the Protection of Venues and Public Spaces from Terrorism
Report
| 
Special
CREST Catalogue
Special
| 5 min read

Guide
Nicola Power, Jennifer Alcock, Mark Levine, Richard Philpot
The Psychology of Interoperability - Study One Summary
Guide
| 
Report
Alexandra Phelan, Jessica White, Claudia Wallner, James Paterson
Misogyny, Hostile Beliefs and the Transmission of Extremism: A Comparison of the Far-Right in the UK and Australia
Report
| 2 min read
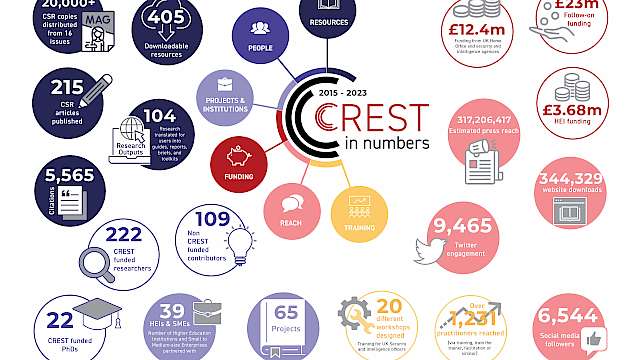
Poster Special
Kayleigh Brennan
CREST in numbers 2023
Poster Special
| 
Report
Lewys Brace
Incel and the Incelosphere: An overview of current research and understanding
Report
| 2 min read

Article
Aldert Vrij
Lie detectors: body language tells us surprisingly little about whether someone is being honest
Article
| 4 min read

Report Poster Special
Ben Lee, Deanna Reder, Cameron Greig
Timeline: Extreme Right-Wing Terrorism in the UK
Report Poster Special
| 1 min read

Article
Lewys Brace
A data-driven analysis of incelosphere engagement by UK-based users
Article
| 5 min read

Policy brief
Lewys Brace
How worried should we be about incel-related violence?
Policy brief
| 3 min read

Thesis Summary
Jonathan Kenyon
Exploring the role of the Internet in the radicalisation process and offending of convicted extremists
Thesis Summary
| 5 min read

Guide
Alexandra Phelan, Jessica White, Claudia Wallner, James Paterson
Introductory Guide to Understanding Misogyny and the Far-Right
Guide
| 10 min read
Report
James Khalil, Martine Zeuthen, Sarah Marsden
A Guide to Deradicalisation & Disengagement Programming
Report
| 4 min read

Poster
Rebecca Stevens
Translating research
Poster
| 
Report
Kat Gibbs, Sophie Nightingale
Bias in Emerging Biometric Systems: A Scoping Review
Report
| 2 min read

Report
Charis Rice, Martin Innes, Jenny Ratcliffe
Situational Threat And Response Signals (STARS): Public-Facing Counter-Terrorism Strategic Communication Campaigns [FULL LITERATURE REVIEW & SUMMARY BRIEFING]
Report
| 3 min read

Poster
Charis Rice, Martin Innes, Jenny Ratcliffe
The STARS Framework
Poster
| 1 min read

Report
Charis Rice, Martin Innes, Jenny Ratcliffe
Situational Threat And Response Signals (STARS): Public-facing Counter-Terrorism Strategic Communication Campaigns [SOCIAL MEDIA ANALYSIS]
Report
| 2 min read

Report
Sarah Marsden, Ben Lee
Conceptualising Protective Factors: Strengths-Based Approaches
Report
| 4 min read

Report
James Hewitt, Ben Lee, Sarah Marsden
Protective Factors in Risk Assessment: Practitioner Perspectives
Report
| 2 min read
