Articles
Short reads covering the latest social and behavioural science research into security threats
new

Article
Vincent Denault, Aldert Vrij
“The eyes can’t lie”: misconceptions about nonverbal communication and why they matter
Article
| new

Article
Mattias Sjöberg
Interpersonal sensemaking: A powerful tool for facilitating cooperation in suspects
Article
| new

Article
Rachel Monaghan, Bianca Slocombe
The Prosecution Landscape for Extremist Actors in the UK
Article
| new
Article
Joel Busher, Sarah Marsden, Leena Malkki
Radicalisation and Counter-Radicalisation Research: Past, Present and Future
Article
| new

Article
Nadine Salman, Zainab Al-Attar
Neurodivergence and Extremism: Considerations for Practice
Article
| new

Article
Austin C. Doctor, Gina Ligon, Samuel T. Hunter
Militant Leadership and the Severity of Terrorism in Conflict Environments
Article
| new

Article
Becky Phythian
Law enforcement information sharing for the 21st Century
Article
| new

Article
Laura Stevens, Tia Bennett, Sarah Rockowitz, Heather Flowe
The role of digital technologies (GBVxTech) in communicating gender-based violence
Article
| new

Article
Anastasia Kordoni, Shengnan Liu, Miriam Koschate-Reis, Mark Levine
Investigating the Influence of Hybrid Social Identities in Online Communities
Article
| new

Article
Marc Kydd, Lynsay Shepherd, Graham Johnson, Andrea Szymkowiak
Love Bytes – Improving Romance Fraud Prevention
Article
| new

Article
Dana Roemling, Jack Grieve
Forensic Authorship Analysis
Article
| new

Article
Laura G. E. Smith
Digital Traces of Offline Mobilisation
Article
| new
Article
Nick van der Klok, Miriam Oostinga, Luke C. Russell, Michael A. Yansick
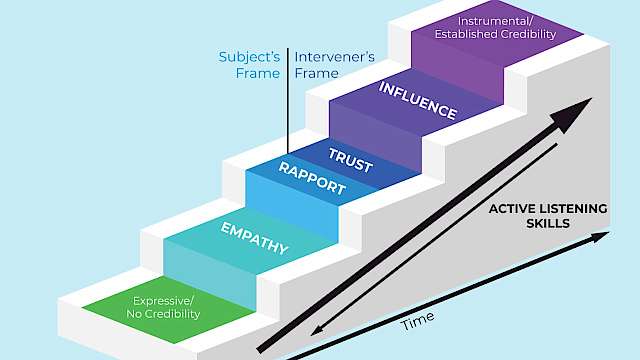
Accelerating Influence: Challenging the Linear Paradigm of Suicide Negotiation
Article
| new
Article
Lina Hillner
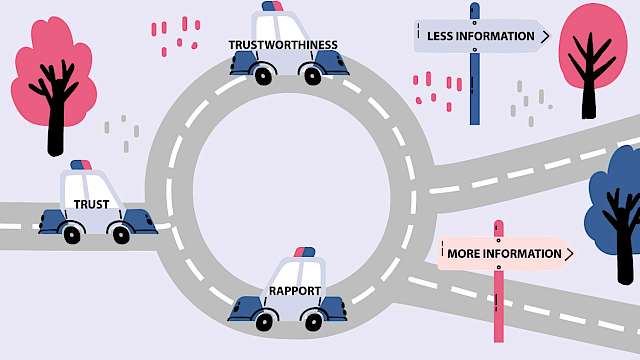
Unexplored Interactions: Disentangling Trustworthiness, Trust and Rapport
Article
| new

Article
David Neequaye
How People Decide What to Disclose in Investigative Interviews
Article
| 
Article
Ben Lee
Risky Business? Siege, subcultures, risk, and unintended consequences
Article
| 
Article
Isabella Orpen
Using Fuzzy Set Qualitative Comparative Analysis to Examine Heterogeneity in Conspiracy Believers
Article
| 
Article
Grace McKenzie
Hiding in plain (web)site
Article
| 
Article
Ricky Green, Imane Khaouja, Daniel Toribio-Flórez, Karen Douglas
Conspiracy Theories: Their Propagation and Links to Political Violence
Article
| 
Article
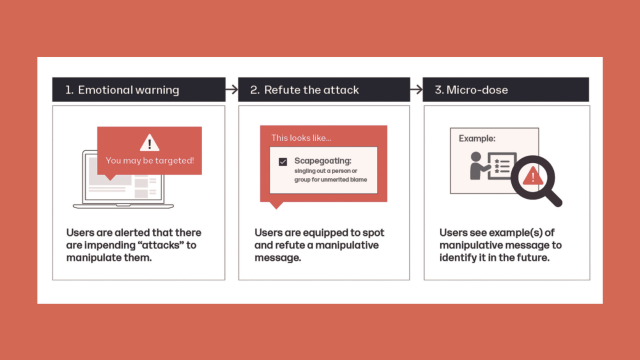
Sander van der Linden
A Psychological Vaccine Against Misinformation
Article
| 
Article
Helen Innes, Andrew Dawson, Martin Innes
OSINT vs Disinformation: The Information Threats ‘Arms Race’
Article
| 
Article
Bettina Rottweiler, Paul Gill
Conspiratorial thinking and far-right extremist attitudes
Article
| 
Article
Sarah Marsden, James Lewis
How do case management tools work to counter radicalisation?
Article
| 
Article
Zoey Reeve
Misleading a Group to Ineffectiveness
Article
| 
Article
Nicola Power, Richard Philpot, Mark Levine
The Psychology of Interoperability: Improving Emergency Services’ Teamwork
Article
| 
Article
William Dance
Addressing Algorithms in Disinformation
Article
| 
Article
Dimitri Pavlounis, Kelsey Davis
What kind of digital media literacy?: Building student resilience to misinformation through evidence-based approaches
Article
| 
Article
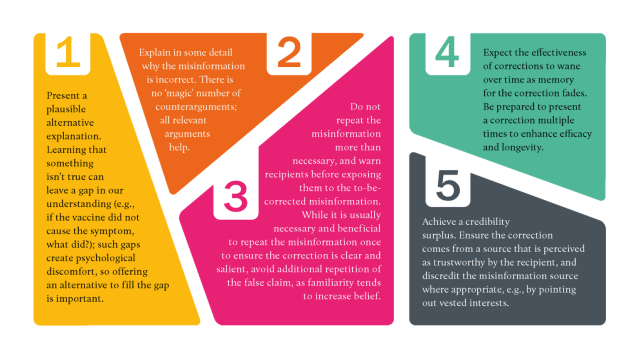
Ullrich Ecker, Toby Prike, Li Qian Tay
Psychological Interventions to Combat Misinformation
Article
| 
Article
Muhsin Yesilada, Paul Grasby
A to Z of Misinformation
Article
| 
Article
Tom Buchanan, Rotem Perach, Deborah Husbands
Why do people share false political information online?
Article
| 
Article
Mujammil Hussain, Jordan Nunan
Understanding Islam and Rapport Building with Muslims
Article
| 
Article
Aldert Vrij
Lie detectors: body language tells us surprisingly little about whether someone is being honest
Article
| 4 min read
Article
Lewys Brace
The ‘incelosphere’ and incel violence: A worsening problem?
Article
| 7 min read

Article
Camilla De Camargo
When the uniform doesn't fit
Article
| 7 min read
Article
Alexandra Phelan, Jessica White, James Paterson, Claudia Wallner
Misogyny and Masculinity: Toward a Typology of Gendered Narratives amongst the Far-Right
Article
| 5 min read

Article
Susan Steen
A Communication Perspective on Resilience
Article
| 5 min read
Article
Lucy Mason
Is ‘Government’ and ‘Innovation’ an oxymoron? Public Sector Innovation: A Practitioner’s Perspective
Article
| 5 min read

Article
Lewys Brace
A data-driven analysis of incelosphere engagement by UK-based users
Article
| 5 min read

Article
Charis Rice, Martin Innes
What’s new, what works? Countering terrorism with public-facing strategic communication campaigns
Article
| 4 min read

Article
Lorraine Hope, Feni Kontogianni, Alejandra De La Fuente Vilar
How did you escape? A rapport-based framework for time-critical questioning involving cooperative interviewees
Article
| 5 min read

Article
Heather Shaw, Charlotte Sibbons, Stacey Conchie, Paul Taylor
Are emerging digital behavioural biometrics able to identify us?
Article
| 4 min read

Article
ChatGPT
AI Innovation Risks & Implications
Article
| 3 min read

Article
Niklas Henderson
The Disinformation Game: Finding New Ways to Fight ‘Fake News’
Article
| 4 min read

Article
Austin C. Doctor, Joel S. Elson, Samuel T. Hunter
Violent Extremism, Innovation, and Recruitment in the Metaverse
Article
| 4 min read

Article
Oli Buckley
Rolling the dice on algorithms: Increasing understanding through boardgames
Article
| 6 min read

Article
James Lewis
Trauma & Violent Extremism: Implications for Interventions
Article
| 7 min read

Article
Heidi Ellis, Emma Cardeli, Stevan Weine
Moving away from ‘Trauma’ towards ‘Trauma and...’
Article
| 7 min read

Article
Kacper Rekawek
Extremist Foreign Fighters in Ukraine
Article
| 4 min read
Article
Stevan Weine, Mary Bunn, Emma Cardeli, Heidi Ellis
Trauma informed Care and Violent Extremism Prevention
Article
| 7 min read

Article
Marika Madfors, Simon Oleszkiewicz, Matthew Jones
Proximity-Based Evidence Disclosure: Enhancing Evidence Reliability
Article
| 4 min read

Article
Alexandria Bradley
Prison safety and security: Exploring the impact of Trauma-Informed Practice and Trauma-Responsive Interventions
Article
| 6 min read

Article
Carmel Joyce, Orla Lynch
Collective Victimhood and the Trauma of Political Violence
Article
| 4 min read

Article
Noah Tucker
What can we learn from exploring the traumatised past of returnees?
Article
| 4 min read

Article
Daniel Koehler
The Radicalisation Pendulum: Introducing a Trauma-Based Model of Violent Extremist Radicalisation
Article
| 4 min read
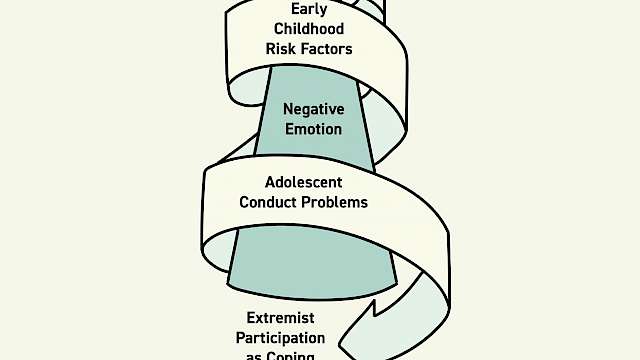
Article
Pete Simi, Steven Windisch
Trauma, Extremism and Criminology
Article
| 4 min read

Article
Anna Naterstad Harpviken
Finding the Story: Expanding the Tale
Article
| 10 min read

Article
Karen Goodall
Trauma Informed Policing
Article
| 4 min read
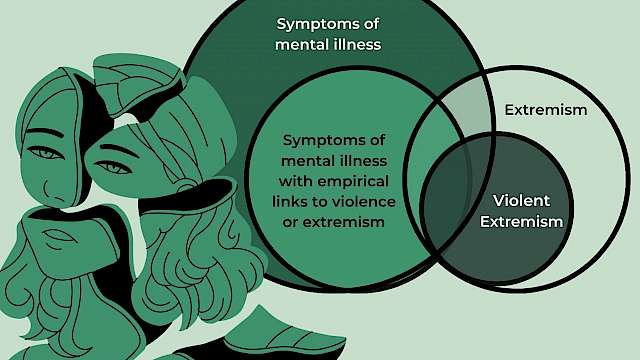
Article
Vivian Khedari
“I have never hurt anybody”
Article
| 7 min read

Article
Ian Barron, Patrick Ashcroft, Gerald Fonville
Police Violence & Child Trauma in the Brazilian Favelas
Article
| 4 min read

Article
Lotta Carlsson
Working with victims of torture
Article
| 6 min read

Article
Michael Niconchuk
What to do about mental health in PVE: insights from Central Asia
Article
| 7 min read
Article
Olivia Brown
Right-wing extremism online: can we use digital data to measure risk?
Article
| 5 min read
Article
Ella Glikson
Emotional over-trust in AI technology
Article
| 3 min read

Article
Lina Hillner
Rapport and trust: What’s the difference?
Article
| 4 min read

Article
Steven Lockey
Recovering from failure: What can security services do to repair trust?
Article
| 4 min read

Article
Rosalind Searle
Trust = confidence + vulnerability The role of the leader
Article
| 3 min read
Article
Paul Taylor
Trusting a Centre model
Article
| 2 min read

Article
Stacey Conchie, Paul Taylor
Trust Signals
Article
| 4 min read

Article
Andreea-Antonia Raducu
Trust Thy Enemy: Trust and Relationship-Building between Source Handlers and Informants
Article
| 4 min read
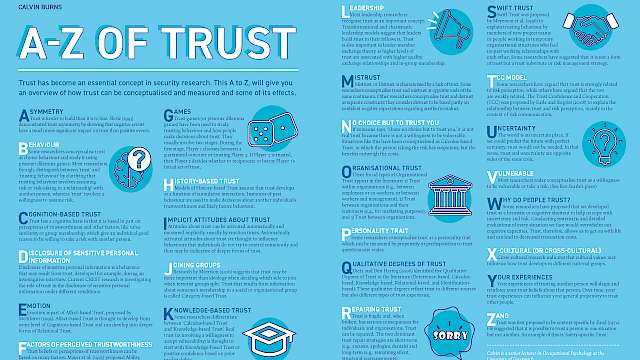
Article
Calvin Burns
A to Z of Trust
Article
| 5 min read

Article
Ben Lee
What is Siege Culture?
Article
| 3 min read
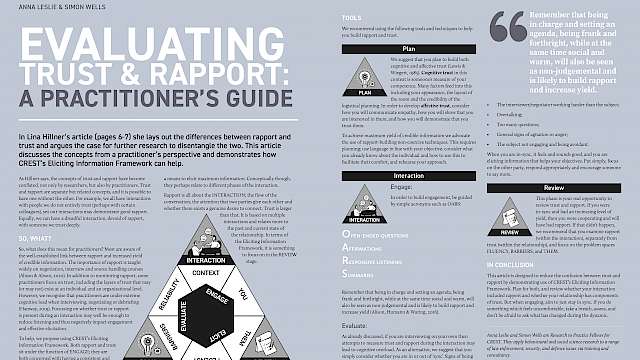
Article
Anna Leslie, Simon Wells
Evaluating Trust & Rapport: A practitioner’s guide
Article
| 4 min read

Article
Stacey Conchie
Trust in Security Contexts
Article
| 4 min read

Article
David Buil-Gil, Jose Pina-Sánchez, Ian Brunton-Smith, Alexandru Cernat
Bad Data, Worse Predictions
Article
| 4 min read

Article
Sophie Nightingale
Identity fraud in the digital age
Article
| 4 min read

Article
Marion Oswald
‘Give Me a Ping, Vasili. One Ping Only’ Why the Success of Machine Learning Depends on Empowered People
Article
| 6 min read
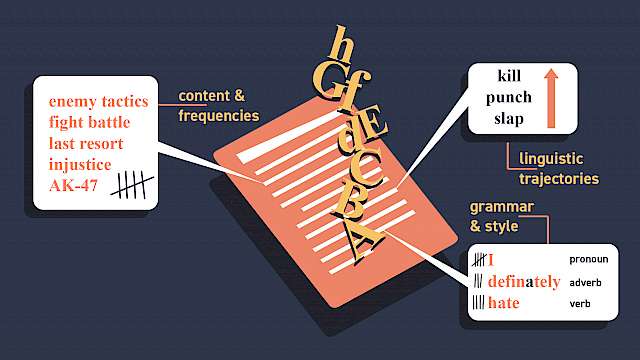
Article
Isabelle van der Vegt, Bennett Kleinberg, Paul Gill
Linguistic Threat Assessment: Challenges and Opportunities
Article
| 5 min read
Article
Emma Boakes
Converging security
Article
| 4 min read

Article
Oli Buckley, Heather Shaw, Leon Reicherts, Richard Philpot, Mark Levine
Technology Lightning Articles
Article
| 7 min read

Article
Erin Grace, Gina Ligon
NCITE: The designated counter terrorism and targeted violence research centre for the US Department of Homeland Security
Article
| 3 min read
Article
Zoe Marchment, Paul Gill
Evaluating the Channel Programme’s Vulnerability Assessment Framework
Article
| 4 min read

Article
Shanon Shah
How (Not) To Make A Violent Copycat: Lessons From ‘Dark Fandoms’
Article
| 4 min read
Article
Chris Baber
Why AI Systems Need to Explain Themselves
Article
| 5 min read

Article
Carl Miller
China’s Digital Diplomacy
Article
| 10 min read

Article
Mapping a new biometrics landscape
Article
| 4 min read

Article
Joel Busher, Gareth Harris, Julia Ebner, Zsófia Hacsek, Graham Macklin
The escalation and inhibition of violence during waves of far-right or anti-minority protests
Article
| 6 min read

Article
Ben Marshall
Putting the Behaviour into Behavioural Analytics
Article
| 4 min read
Article
Anna Leslie
The Eliciting Information Framework: A Vehicle For Research Into Practice
Article
| 5 min read
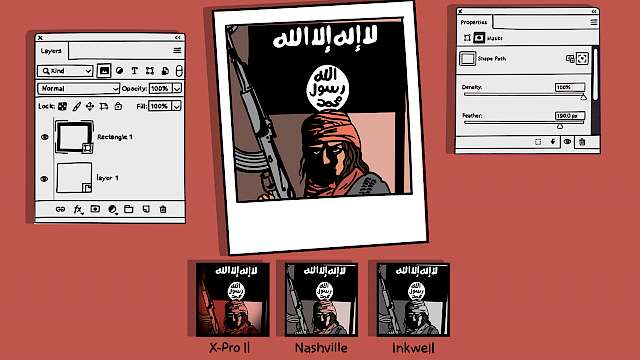
Article
Simon Copeland
Islamic State, Filters, and Photoshop
Article
| 4 min read

Article
Andrew Silke, John F. Morrison, Heidi Maiberg, Chloe Slay, Rebecca Stewart
The Phoenix Model: Disengagement And Deradicalisation
Article
| 6 min read

Article
Lorraine Bowman Grieve
COVID-19 Conspiracy In Ireland And The Far-Right Nexus
Article
| 3 min read

Article
Jason Nurse
Balancing Cybersecurity and Privacy in the Remote Workforce
Article
| 4 min read

Article
Laurence Alison, Emily Alison, Sarah Robertson, Michael Humann
The Ground TRUTH After-Action Review Tool
Article
| 4 min read
Article
Stephan Lewandowsky, Muhsin Yesilada
The “Infodemic”, Inoculation, And Insurrections
Article
| 4 min read
Article
Olivia Brown
Multi-Agency Emergency Response
Article
| 4 min read

Article
Jordan Nunan, Ian Stanier
Intelligence gathering during a pandemic
Article
| 4 min read

Article
Lorraine Hope, Rachel Zajac, Maryanne Garry
Where was I last Wednesday?
Article
| 3 min read
Article
Nathan Smith, Emma Barrett
Lessons From A Rapid Response
Article
| 6 min read

Article
Michele Grossman
How Has COVID-19 Changed The Violent Extremist Landscape?
Article
| 4 min read

Article
Lewys Brace
A Short Introduction To The Involuntary Celibate Sub-Culture
Article
| 10 min read

Article
Ben Lee
Only Playing: Extreme-Right Gamification
Article
| 4 min read

Article
John F. Morrison, Andrew Silke, Heidi Maiberg, Chloe Slay, Rebecca Stewart
The Role Of (Dis)Trust In Disengagement And Deradicalisation
Article
| 6 min read

Article
Steven Watson
Risk, benefits, and the affect heuristic in security behaviours
Article
| 6 min read

Article
Monica Lloyd
The A–Z Of Extremism Risk Assessment
Article
| 5 min read

Guide Article
Ian Stanier, Jordan Nunan
FIREPLACES And Informant Motivation
Guide Article
| 5 min read

Article
Brooke Rogers, Julia Pearce, David Parker, Lasse Lindekilde
Communicating effectively with the public about terrorism in crowded places
Article
| 5 min read

Article
Nathan Smith
Resilient Performance Of Defence And Security Personnel
Article
| 5 min read

Article
Bettina Rottweiler, Paul Gill
Risk Factors for Violent Extremist Beliefs and Parallel Problem Areas
Article
| 3 min read

Article
Caroline Logan
Violent Extremism: The Assessment And Management Of Risk
Article
| 7 min read
Article
Emily Collins, Phillip Morgan, Dylan Jones
If This Then…What? Security And Privacy In Trigger-Action Systems
Article
| 3 min read
Article
Nadine Salman, Paul Gill
Terrorism Risk Assessment: What Makes A ‘Good’ Risk Assessor?
Article
| 4 min read

Article
David McIlhatton, Rachel Monaghan
Protecting Publicly Accessible Locations From Terrorism
Article
| 5 min read

Article
Steven Watson
Risk, benefits, and the affect heuristic in security behaviours
Article
| 6 min read

Article
Simon Oleszkiewicz
The Adaptable Law Enforcement Officer
Article
| 5 min read

Article
The Transnational Extreme-Right: Past, Present, and Future
Article
| 1 min read

Article
Matthew Fields
Proof of Life or Death?
Article
| 4 min read

Article
Ben Lee
Think Global, Act Local: Reconfiguring Siege Culture
Article
| 5 min read

Article
Emma Williams, Emma Slade
What Influences Consumer Adoption and Secure Use of Smart Home Technology?
Article
| 3 min read

Article
Duncan Hodges
Mapping Smart Home Vulnerabilities to Cyber-Enabled Crime
Article
| 3 min read

Article
Florence Keen
After 8chan
Article
| 6 min read

Article
Blyth Crawford
/K/ and the Visual Culture of Weapons Boards
Article
| 10 min read

Article
Michele Grossman, Paul Thomas
Community Reporting on Terrorism: Bystanders Versus Social Intimates
Article
| 4 min read

Article
Paul Thomas, Michele Grossman
Community Reporting of Terrorist Involvement During Covid-19
Article
| 4 min read

Article
Peter Lee
Psychological trauma – it’s what happens to other people. Right?
Article
| 4 min read

Article
Ben Lee
Blind Networks in the Extreme-Right
Article
| 4 min read

Article
Ben Lee
A Short Guide to Narratives of the Far-Right
Article
| 3 min read

Article
Nick Neave
The Risks of Digital Hoarding
Article
| 3 min read

Article
Oli Buckley
CLICKA
Article
| 4 min read

Article
Kristoffer Geyer
Understanding digital traces
Article
| 4 min read
Article
Emma Boakes
How Do Security Teams Collaborate To Understand Threats to Their Building Management Systems?
Article
| 4 min read

Article
Olivia Brown
Teamwork in Extreme Environments: Identifying Challenges and Generating Solutions
Article
| 4 min read

Article
Jordan Nunan
Developing an Evidenced-Based Approach to Enhance Recall of Intelligence
Article
| 4 min read

Article
Joel Busher, Gareth Harris, Graham Macklin
Credibility contests and the ebb and flow of anti-minority activism
Article
| 10 min read

Article
Rosie Mutton
Understanding the Roles Women Play in Violence Extremism and Why it Matters
Article
| 4 min read

Article
Jordan Nunan
Increasing Accurate Recall in Human Sources
Article
| 3 min read

Article
Alan Ogle
Remote Combat Readiness and Resiliency
Article
| 5 min read
Article
Natalia Trujillo, Juan Esteban Ugarriza
The Deep Effects of Armed Conflict: Intervening in the Complexities of Post-Conflict Reconciliation
Article
| 5 min read

Article
Susie Ballentyne
Refugee Resilience: Where Should We Be Looking?
Article
| 5 min read

Article
Mustafa Sarkar
Developing Resilience for Sustained Success
Article
| 7 min read

Article
Jason Nurse
Cyber Resilience: What Is It and How Do We Get It?
Article
| 5 min read

Article
Aaron Roberts, Neville Stanton
Go with the (Information) Flow? How to Develop more Resilient Sociotechnical Systems
Article
| 4 min read

Article
Nick Crossley
Strengths and Vulnerabilities in (Covert) Network Structure
Article
| 4 min read

Article
Emma Grace
Bouncing Back: Stress and Resilience in Al-Qaeda Terrorists
Article
| 6 min read

Article
Lorraine Hope
From the Lab to Operational Response: Examining the Impact of Stress On Memory for High Pressure Incidents
Article
| 5 min read

Article
Marc Jones
Challenge or Threat: Understanding How People Cope in Demanding Environments
Article
| 5 min read

Article
Jesper Corneliussen, Anders Kjaergaard
Conflict Management in Extreme Environments
Article
| 4 min read

Article
Kristine Endsjø
Affect and emotion in extremist discourse
Article
| 3 min read

Article
Abbie Marono
Is nonverbal mimicry an important tool in eliciting information?
Article
| 3 min read

Article
Christina Winters
Increasing Self-Disclosure in Interviews
Article
| 4 min read

Article
Noémie Bouhana
Analysing Lone-Actor Terrorism in Context
Article
| 5 min read

Article
Duncan Hodges
A to Z of Data
Article
| 3 min read

Article
Joel Busher, Donald Holbrook, Graham Macklin
Explaining Non- Or Limited Escalation Of Violence: The role of ‘Internal Brakes'
Article
| 3 min read

Article
Sarah Marsden
Countering Violent Extremism: A Guide to Good Practice
Article
| 4 min read

Article
Pamela Hanway
Cognitive Load at Interview: The Interviewer's Perspective
Article
| 3 min read
Article
Feni Kontogianni
Untangling the past: remembering details of repeated events
Article
| 3 min read

Article
Paul Taylor
From data to datum: What should I do in this case?
Article
| 4 min read
Article
Debi Ashenden
Algorithmic Decision Making
Article
| 5 min read
Article
Joanne Hinds
Behaviour Prediction: The Challenges and Opportunities of Big Data
Article
| 4 min read

Article
Pip Thornton
Words as Data: The Vulnerability of Language in an Age of Digital Capitalism
Article
| 5 min read

Article
Ryan Boyd, Paul Kapoor
Psychological Profiling and Event Forecasting Using Computational Language Analysis
Article
| 5 min read

Article
Debi Ashenden
Data and the Social and Behavioural Sciences
Article
| 4 min read

Article
Lorraine Hope, Wayne Thomas
A to Z of Influence Tactics and Topics
Article
| 4 min read

Article
Gordon Wright, Nelli Ferenczi
Cross-cultural dimensions impacting persuasion and influence in security contexts
Article
| 4 min read

Article
Robert Nash
In the misinformation age, remember that your memories might be fake news
Article
| 5 min read
Article
Stephan Lewandowsky, Sander van der Linden, John Cook
Can we inoculate against fake news?
Article
| 4 min read

Article
Emily Corner
Mental Disorder in Terrorism, Mass Murder, and Violence: Moving away from Pathologising Grievance
Article
| 5 min read

Article
Emily Alison, Laurence Alison
Persuasion and Influence or Genuine Connection and Rapport
Article
| 5 min read

Article
Samantha McGarry
The Far Right and Reciprocal Radicalisation
Article
| 4 min read

Article
Susan Brandon
Using Stereotypes to Prepare for Interviews
Article
| 4 min read
Article
Robert Cialdini, Steve Martin
The Power of Persuasion and Pre-Suasion to Produce Change
Article
| 5 min read

Article
Wayne Thomas, Lorraine Hope
Try To See Things My Way? The Role Of Perspective Taking In Eliciting Information
Article
| 4 min read

Article
Rosalind Searle, Charis Rice
Positively Influencing Individuals During Organisational Change
Article
| 15 min read

Article
Kirk Luther, Brent Snook, Timothy Moore
Lingering Problems With The Mr Big Technique
Article
| 5 min read

Article
Heather Flowe
Informants Under The Influence: Can Intoxicated Informants Provide Accurate Information?
Article
| 3 min read

Article
Simon Henderson
The Trade Of The Tricks: How Principles Of Magic Can Contribute To National Security
Article
| 5 min read

Article
Christopher McDowell
Displacement and Transition Risks
Article
| 4 min read

Article
Sheryl (Prentice) Menadue
Influence In Extremist Messaging
Article
| 4 min read
Article
Andrea Pereira, Jay Van Bavel
The Partisan Brain: Why People Are Attracted To Fake News And What To Do About It
Article
| 5 min read

Article
David Neequaye
Subtle Influence and Information disclosure: How Priming Works in Intelligence Interviews
Article
| 4 min read

Article
Paul Taylor
Communicating across cultures
Article
| 10 min read
Article
Nicola Power
Terror attacks: How psychological research can help improve the emergency response
Article
| 4 min read

Article
Suzanne Newcombe
Disengagement: Lessons from Cults and Sectarian Groups
Article
| 4 min read
Article
Simon Wells
Transitions in negotiation: From crisis to success
Article
| 6 min read
Article
Sarah Marsden
Reintegrating Extremists: ‘Deradicalisation’ and Desistance
Article
| 5 min read

Article
Jordan Nunan, Becky Milne
Turning research into practice in investigative interviewing
Article
| 3 min read

Article
Aldert Vrij, Ronald P. Fisher
Which Lie Detection Tools are Ready for Use?
Article
| 4 min read

Article
Rosalind Searle, Charis Rice
How Messing with Employee Pensions Can Backfire on Companies
Article
| 4 min read

Article
Martin Innes
Russian Influence And Interference On Twitter Following The 2017 UK Terrorist Attacks
Article
| 3 min read

Article
David Omand
Intelligence ethics: not an oxymoron
Article
| 5 min read

Article
Tina Wilchen Christensen
From extremists to democratic citizens
Article
| 6 min read

Article
Nicola Power
A to Z of Decision Making
Article
| 4 min read

Article
Samantha Mann
How does a smuggler behave?
Article
| 4 min read

Article
Miriam Oostinga
Communication error handling in suspect interviews and crisis negotiations
Article
| 3 min read

Article
Jan-Willem Bullée
Social Engineering: From Thoughts to Awareness
Article
| 3 min read

Article
Neil Ferguson
Understanding Engagement in Violent Extremism in Northern Ireland
Article
| 3 min read

Article
Laurence Alison, Michael Humann, Sara Waring
Communicating with casualties in emergencies
Article
| 3 min read

Article
Paul Gill
8 things you need to know about terrorist decision-making
Article
| 4 min read
Article
Julie Gore, Paul Ward, Gareth Conway
Naturalistic Decision Making and Uncertainty
Article
| 2 min read

Article
Simon Ruda
Measuring decision making
Article
| 4 min read

Article
Renate Geurts
Why professionals are needed to assess threats of violence
Article
| 3 min read

Article
Nicola Power
Decision making during emergencies: what have we learned and where do we go from here?
Article
| 4 min read
Article
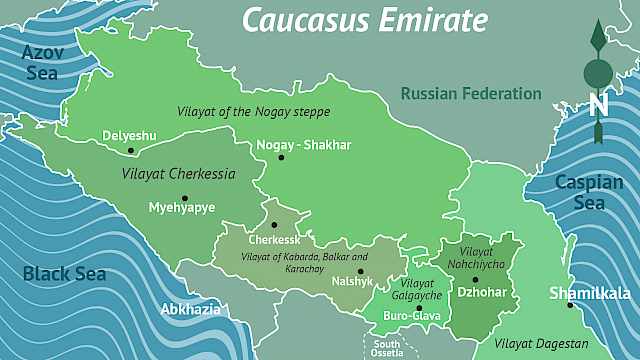
Cerwyn Moore, Mark Youngman
New report on Russian-speaking Foreign Fighters
Article
| 2 min read

Article
Jasjit Singh
Sikh Activism in Britain
Article
| 4 min read

Article
Jasjit Singh
Religious transmission among young adults in the digital age
Article
| 4 min read

Article
Awais Rashid, Sylvain Frey
Cyber security decisions: how do you make yours?
Article
| 3 min read
Article
Emma Barrett, Nathan Smith
Decision making under stress
Article
| 5 min read

Article
Mark Youngman
Learning from ideological variance and change
Article
| 3 min read

Article
Michele Grossman, Paul Thomas
What are the barriers to reporting people suspected of violent extremism?
Article
| 3 min read
Article
Martin Everett
Covert Networks
Article
| 2 min read

Article
Rosalind Searle, Charis Rice
Trust and Insider Threat: Ensuring We Don’t Look Back – or Forward – in Anger
Article
| 3 min read
Article
Stephane Baele, Katharine Boyd, Travis Coan
Extremist Prose as Networks
Article
| 3 min read

Article
Kate Muir
What is rapport and how can you increase it?
Article
| 3 min read

Article
Mia Bloom
Islamic State messaging on Telegram
Article
| 3 min read

Article
Michele Grossman, Paul Thomas
Community Reporting: The key to defeating terrorism?
Article
| 4 min read

Article
Thilo Gross
Things that spread: Epidemics on networks
Article
| 4 min read
Article
Using Networks to Predict the Impact of ‘Bad Apples’ on Team Performance
Article
| 3 min read

Article
Dorothy Carter, Cynthia Maupin
Leadership Is a Social Network: Implications for Security
Article
| 4 min read

Article
Katharina Karcher
Can female participation in political violence lead to social progress? – a case study from Germany
Article
| 3 min read
Article
Christos Ellinas
Predicting and Preparing for the Failure of Complex Systems
Article
| 4 min read

Article
Adam Joinson, Brittany Davidson
Why networks matter
Article
| 3 min read

Article
Jordan Nunan
Gathering Full and Faithful Human Intelligence
Article
| 3 min read

Article
Ben Lee
Understanding the far-right landscape
Article
| 2 min read

Article
Charis Rice, Rosalind Searle
Trust and Citizenship: The Insider Threat
Article
| 3 min read

Article
John Horgan
The Lost Boys
Article
| 6 min read

Article
Mark Youngman
Lessons from the decline of the North Caucasus insurgency
Article
| 4 min read

Article
Donald Holbrook
The Islamic State and Ayman al-Zawahiri’s ‘alternative jihad’
Article
| 3 min read

Article
Nicholas Ryder
Is there something missing? Terror finances and the UK review of economic crime
Article
| 3 min read

Article
Nelly Lahoud
What Next for Islamic State?
Article
| 4 min read

Article
Christopher McDowell
Sri Lanka, Diaspora Politics, and The End of Violence
Article
| 4 min read

Article
Cerwyn Moore
Transnational Activism Through the Ages
Article
| 3 min read
Article
Feni Kontogianni
Memory recall: The challenge of eliciting reliable information
Article
| 3 min read

Article
Olivia Brown
Teamwork in extreme environments
Article
| 3 min read
Article
George Joffé
Regional Guide: Tunisia
Article
| 3 min read
Article
Wolfram Lacher
Regional Guide: Libya
Article
| 3 min read

Article
Kris Christmann
Manchester attack: an 'arms race' against ever adapting terror networks
Article
| 4 min read

Article
Michael Axworthy
Regional Guide: Iran
Article
| 3 min read

Article
Joas Wagemakers
Regional Guide: Jordan
Article
| 3 min read

Article
Elisabeth Kendall
Regional Guide: Yemen
Article
| 4 min read

Article
Paul Taylor
7 Things Worth Knowing About Groups
Article
| 4 min read

Article
Joe Uscinski
Everyone is a conspiracy theorist
Article
| 4 min read

Article
Cerwyn Moore, Timothy Holman
Remainers and leavers: Foreign fighters after the ‘Islamic State’
Article
| 5 min read

Article
Iain Edgar
After Islamic State: the place of night dream inspiration and propaganda
Article
| 2 min read

Article
Emma Williams
What Makes People Susceptible to Malevolent Influence Online?
Article
| 3 min read

Article
Rosie Mutton
The role of gender in violent extremism
Article
| 3 min read

Article
Mark Youngman
After St Petersburg: Russia and the Threat from Central Asian Terror Networks
Article
| 5 min read

Article
Lynn Weiher
How do we measure rapport in interviews?
Article
| 3 min read

Article
James Lewis
How do teachers engage with Prevent?
Article
| 4 min read

Article
Simon Copeland
The Importance of Terrorists’ Families and Friends
Article
| 4 min read
Article
Mark Youngman
Russia's domestic terrorism threat is serious, sophisticated, and complex
Article
| 4 min read

Article
Ben Lee
Grassroots counter messaging in the UK
Article
| 3 min read

Article
Irina Tache
Connecting Culture to Deception Detection
Article
| 4 min read

Article
Kim Knott, Matthew Francis
Are converts to Islam more likely to become extremists?
Article
| 5 min read

Article
Kim Knott, Ben Lee
How does the family pass on religion?
Article
| 3 min read

Article
Simon Copeland
Transmitting Terrorism: A Family Affair?
Article
| 3 min read

Article
Nick Donnelly, Anne Hillstrom, Natalie Mestry
Just another face in the crowd – what makes spotting unfamiliar faces difficult?
Article
| 3 min read

Article
Emma Williams, Debi Ashenden
Phishing Scams Are Becoming Ever More Sophisticated And Firms Are Struggling To Keep Up
Article
| 4 min read
Article
Amanda van Eck Duymaer van Twist
How beliefs may come and go: a brief overview of a ‘cult career’
Article
| 3 min read

Article
Sarah Marsden
From ideological material to targeting choice in leaderless jihadist
Article
| 3 min read

Article
Aristotle Kallis
‘Reverse waves’: how radical ideas spread and take hold
Article
| 4 min read

Article
Ben Lee
A different perspective on CVE
Article
| 4 min read

Article
Ben Lee, Elizabeth Morrow
Transmission in context
Article
| 4 min read
Article
Jonathan Scourfield
Learning to be a Muslim
Article
| 3 min read

Article
John F. Morrison
Transmitting Legitimacy and Victimhood: Violent Dissident Irish Republicanism
Article
| 3 min read

Article
Lynn Davies
Disrupting transmission of extremist messages through education
Article
| 3 min read

Article
Kim Knott
Why transmission?
Article
| 3 min read

Article
Lorraine Hope, Matthew Francis
When does inconsistency matter?
Article
| 2 min read

Article
Matthew Williams, Pete Burnap
Cyber crime and the social web
Article
| 3 min read

Article
Linda Woodhead
The continuing growth of religious extremism and how to counter it
Article
| 6 min read

Article
Debi Ashenden
Employees Behaving Badly
Article
| 4 min read

Article
Lorraine Hope
How does memory work?
Article
| 3 min read

Article
Joanne Hinds
What is the role of technology in an emergency?
Article
| 4 min read

Article
René Rydhof Hansen, Lizzie Coles-Kemp
Everyday Security: A Manifesto for New Approaches to Security Modelling
Article
| 3 min read

Article
Tim Stevens
Cyber security and the politics of time
Article
| 4 min read

Article
Marcus Rogers
Hacker Mindset
Article
| 3 min read
Article
Jeremy Watson, Emil Lupu
PETRAS: Cyber Security of the Internet of Things
Article
| 3 min read

Article
Christian Meissner, Susan Brandon
Expanding the frontiers of interrogation research and practice
Article
| 3 min read

Article
Debi Ashenden
Fact Check: The Cyber Security Attack Surface
Article
| 4 min read
Article
Heather Shaw, David Ellis
Apple or Android? What your choice of operating system says about you
Article
| 2 min read

Article
Nicholas Ryder
The Criminal Finances Bill
Article
| 4 min read

Article
Ben Lee
Understanding the counter-jihad
Article
| 2 min read
Article
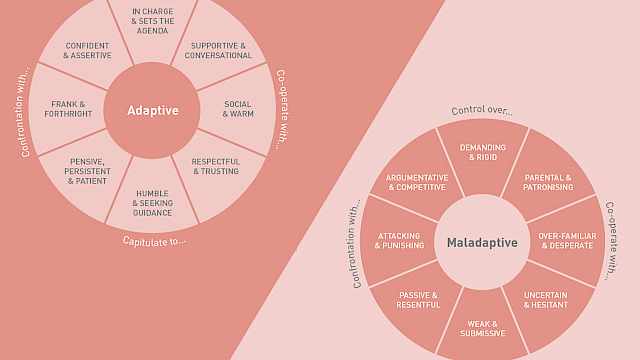
Laurence Alison, Michael Humann, Sara Waring
Building good rapport in interviews
Article
| 4 min read

Article
Debi Ashenden
Creativity and Cyber Security
Article
| 2 min read

Article
Paul Taylor
The A–Z of Information elicitation
Article
| 3 min read

Article
Robert A. Fein
Improving practice through research: The US and the Study on Educing Information
Article
| 2 min read
Article
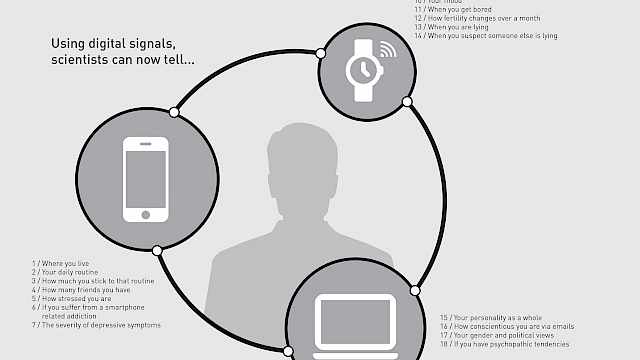
David Ellis, Lukasz Piwek
The future of wearable technology
Article
| 2 min read

Article
Elizabeth Morrow
Loyal footsoldiers: The attractions of EDL activism
Article
| 5 min read

Article
Adam Joinson, Emma Williams
Eliciting Information Online
Article
| 3 min read

Article
Paul Taylor
The promise of social science
Article
| 3 min read

Article
Simon Oleszkiewicz
Eliciting information the friendly way: Conceptualising the Scharff Technique
Article
| 3 min read

Article
Becky Milne
Let them be heard: Enabling communication and recall of forensic interviewees
Article
| 1 min read

Article
Lorraine Hope
Memory at the sharp end: the psychology of eliciting information
Article
| 1 min read

Article
Emma Barrett
The role of trust in deciding which terrorist faction to join
Article
| 2 min read

Article
Sheryl (Prentice) Menadue
How Technology Could Help Predict Terrorist Attacks
Article
| 3 min read

Article
Nicholas Ryder
Where does the Islamic State get its money?
Article
| 4 min read
Article
Cerwyn Moore, Elizabeth Morrow
What role do women play in violent extremism?
Article
| 3 min read

Article
Kim Knott
What are the Five Pillars of Islam?
Article
| 3 min read

Article
Emma Barrett, Matthew Francis
The Cognitive Interview: How Research has improved Practice
Article
| 2 min read

Article
Nicola Power
Joint Decision Making in Real-World Emergencies: Recommendations for Improving the Joint Decision Model
Article
| 4 min read

Article
Joanne Hinds
How Does Phishing Work?
Article
| 3 min read

Article
Emma Barrett, Matthew Francis
Terrorists’ use of messaging applications
Article
| 3 min read

Article
Ben Lee
One peaceful march doesn't change Pegida's disturbing ideology
Article
| 3 min read

Article
Debi Ashenden
Your Employees: The Front Line in Cyber Security
Article
| 10 min read

Article
Matthew Francis
Research drives understanding and disruption of terrorism
Article
| 4 min read

Article
Matthew Francis
Paris attacks: there is no simple explanation
Article
| 3 min read
Article
Debi Ashenden
TalkTalk Data Breach Is a Wake Up Call for CEOs
Article
| 3 min read
